2 minutes
Has my SOC2 Type II audit tested a HITRUST control?
HITRUST Program Methodology requirement: map an in-scope control to a third-party audit.
HITRUST Assurance Advisory 2019-010 requires HITRUST external assessors “to map the applicable / scoped HITRUST CSF requirement statements to the controls / requirements tested in the third-party audit”. Organizations under assessment and assessors alike sometimes assume SOC2 Type II audits always test in-scope controls for HITRUST assessments. Unfortunately, SOC2 Type II audits do not always test specific controls in a HITRUST Validated Assessment (now r2).
Anyone who has ever been part of a HITRUST r2 Assessment knows it drains resources from the assessor organizations and the client. External Assessors regularly deal with stressed project coordinators rushing assessments to reduce cost and meet contract deadlines. Clients either assume a SOC2 Type II report automatically satisfies an applicable HITRUST control or hope the external assessor will not verify the report.
How can External Assessors convince an assessed organization their third-party does not support a control in its SOC2 Type II report? Assessors can use a careful combination of HITRUST documentation along with the SOC2 Type II report.
Example: scans for unauthorized wireless access point
SOC2 Type II audits rarely tests whether an organization runss quarterly scans for unauthorized wireless access points. The HITRUST 0505.09m2Organizational.3 control states the following.
“1. Quarterly scans are performed to identify unauthorized wireless access points, and appropriate action is taken if any unauthorized access points are discovered.”
Process: use mapping to verify report
The assessor use the control’s HITRUST identifier and the HITRUST SOC2 resources to pinpoint the Trust Services Criteria. Then the assessor searches for these sections in the third-party report.
- 09m of the 0505.09m2Organizational.3 ID denotes Network Controls.
- 09m maps to CC6.1, CC6.6, CC6.7, A1.1, and A1.2.
- Search the SOC2 Type II report for CC6.1, CC6.6, CC6.7, A1.1, and A1.2
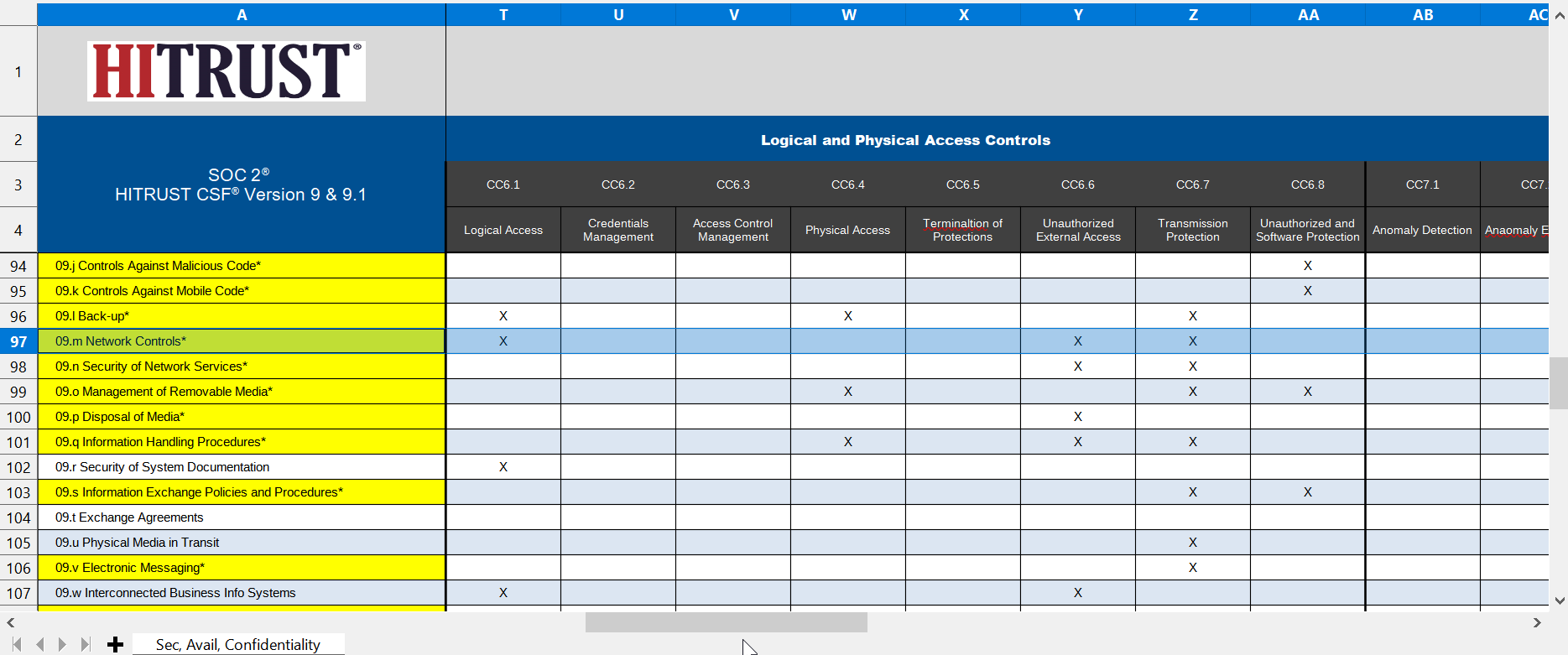
If the report does not document test findings for these SOC2 Type II controls then the audit did not test the HITRUST control requirement. The assessor documents the findings, communicates them to the client, and scores the control as deficient. Ideally, this gap would be found during pre-assessment. If not, then the organization going through the assessment may have to take a CAP for the control.
362 Words
2022-03-25 00:00